Next: Contributions
Up: Bringing Role-Based Access Control
Previous: Abbreviations
For several years, there has been a clear trend in research and in the
market place towards distributed applications and techniques. The days
of centralized and monolithic software systems are past. Today,
concepts like client/server, the Internet,
Intranets, distribution, virtual organizations,
tele-commuting and Cyberspace are in vogue. These
phenomena all have one thing in common, namely the underlying need for
communications, often taking place over public networks.
Unfortunately, however, communicating information over a network
introduces vulnerabilities. For instance, information might get
distorted in transit (accidently or on purpose), eavesdropping might
result in sensitive information being revealed, or the remote node we
are communicating with might in fact be someone other than we think.
Another issue that arises when more and more applications become
``distributed'' is how to cater for those existing systems that we are
loath to do away with, either because they function well today or
because they would be very expensive to replace.
Even if a secure means of communications is provided, there are still
many other security issues to be considered. In all systems, it is
important to manage the use of resources in a secure and efficient
way. For reasons of confidentiality, integrity, economy, and others,
access to programs, files, printers, etc. in a system is very often
subject to access control. To get a working access control
system, two equally important issues must be considered. There must
exist technical solutions that make it possible to put the access
control system in place and, equally important, it must be possible to
manage and administrate access control information in an efficient and
expeditious way.
Consider the following example:
- Acme General Hospital
- has recently invested in a new computer
system that among other features allows for electronic storage of
patient records and electronic transfer of laboratory test results
and X-ray images. In a hospital environment, demands on security are high.
Consistency and availability of data must be guaranteed at all
times. Ethics as well as legislation also put the demands for
confidentiality in focus.
For several years at Acme General there has been a constant
personnel shortage due to tight budgets and other factors. As a
consequence, doctors, nurses, and secretaries must often move
between wards to meet minimal staffing requirements. Short-time
extra replacements are not uncommon either. Given the mobility of
personnel, the designers of the new computer system realized early
on that access control could not be managed on an individual basis.
Instead, the designers decided to go for a role-based
approach.
First of all, the organization of a typical ward was analyzed and a
set of roles was identified. These were secretary,
nurse, head nurse, physician, senior physician
and head physician . Secondly, access control in the
computer system was tailored to differentiate access to patient
records and other resources according to
. Secondly, access control in the
computer system was tailored to differentiate access to patient
records and other resources according to

the role(s)

a
user has. By using this indirect way of expressing permissions it
was possible to put in place and verify access control rules without
knowing who the individual users of the system would be.
Once a system is in place, it is necessary to allow
individual users to take on roles. At Acme General, every employee
who needs access to the computer system (and that is almost
everyone) is provided with a personal smart card that is used
together with a pass-phrase to identify the user to the system along
the same principles as for automatic teller machines. As every
individual is personally accountable for her actions,
establishing identity is very important, even though operations
in the computer system are performed in the capacity of some role. At
Acme, every computer terminal has a card reader into which the user
must insert her smart card in order to activate the terminal. To
discourage the possible use of someone else's identity, for instance
if someone has forgotten a card in the reader, a policy has been
implemented that requires users to reassert individual identity
when an update transaction is performed.
Due to the strained circumstances of the personnel, the assignments within a
ward of individuals to roles vary quite frequently. Before the start
of each working week, the head physician finalizes a
duty roster that contains the current assignments, including
information about who will be acting as head physician.
The scenario illustrates the main idea of role-based access
control, RBAC. An indirection in the assignment of access
rights can greatly reduce the administrative effort needed to
maintain consistency in the system. Another important property of
RBAC highlighted in the example is that access control
assignments can be performed without knowledge of the actual
individuals who will fill the roles.
In this thesis we study how role-based access control can be brought
to distributed systems. In order to introduce access control in
distributed systems, one has to deal with many of the vulnerabilities
to communications arising from distribution, as well as other
problems. For example, in a distributed system, it is necessary to
decide where access control information (ACI) should be
stored and managed. Another problem to be addressed is how ACI
should be retrieved by various security mechanisms.
Figure 1.1 shows schematically the three main
logical components in a secure distributed system. A typical situation
is where a client wishes to call upon the services of some remote
server. In addition to the client and server, somewhere in the system
security information and security services are also
provided. This information and these services are needed for
ensuring secure communications and for the enforcement of access
control.
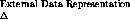
Figure 1.1: Logical components in a secure distributed system.




Next: Contributions
Up: Bringing Role-Based Access Control
Previous: Abbreviations
matgu@ida.liu.se
 . Secondly, access control in the
computer system was tailored to differentiate access to patient
records and other resources according to
. Secondly, access control in the
computer system was tailored to differentiate access to patient
records and other resources according to