Figure 2.4: Encrypted communication.




As was discussed in the previous section, it is apparent, and disconcerting, that distribution seems to open many possibilities for malicious attackers. In this section we introduce some building blocks that are important in order to counter these threats. The presentation here is kept simple and mainly introduces concepts and general principles. For a more in depth introduction to these topics we refer to chapter chapter 6 and to the literature. For instance [Pfl97] gives a good overview of the area.
The building blocks we introduce are cryptography and confidentiality, authentication and non-repudiation, and access control. Combining these building blocks into functioning systems is an important and sometimes difficult job. However, existing frameworks (see chapter 7) and plug-in libraries help make the task manageable.
Codes, ciphers, and secret writing has been used since ancient times to protect sensitive information from falling into wrong hands. Cryptography is about transforming a text, or arbitrary message, into something that is totally illegible, called ciphertext or cryptogram. It should also be possible to transform the ciphertext back into the original message, but only for the designated recipient.

Figure 2.4: Encrypted communication.
In figure 2.4, Bob sends a message to Alice. To secure the transmission from eavesdropping, Bob first applies a cryptographic algorithm to the message. The algorithm is a function that takes two inputs, the message and a key, and produces a ciphertext. Different keys produce different ciphertexts. To be able to read Bob's message, Alice runs the ciphertext through a cryptographic algorithm that is the inverse function of the one Bob used. The deciphering function also requires that Alice supplies the correct key. Distribution and management of the keys needed for encrypted communications are complex issues that are subject to current research.
An important issue for secure communications is to be able to positively identify the remote party. If this is not possible, an impostor might undetected take the place of a communicating party.
A process where one party proves its identity to another is called authentication. In most techniques for authentication, an entity proves its identity by demonstrating it possesses something that it is known to be possessed only by that entity. For instance, a common method for authentication of computer users is through passwords. This method works on the assumption that the password is only known to the system and the user, therefore, the system can conclude a user is who she claims to be if she can provide the password that matches her identity.
Another form of authentication is when a receiver wants to positively establish the identity of an originator of a message. For such purposes cryptographic techniques are used to generate a digital signature that is attached to the message. Digital signatures are described in section 6.1.4. A discussion about authentication in general can be found in section 6.2.
In many situations it is desirable for a sender of a message to obtain a receipt showing that a message was sent, and received intact, at a specific time. Examples are many, such as receipt of payment, proof that an application document has arrived on time, and proof that an addressee has received an email.
To make this possible, a common solution is to use a trusted third party that provides a non-repudiation service. A non-repudiation service uses cryptographic techniques to create an unforgeable receipt that can be uniquely associated with a message. When the service creates a receipt, it also inserts a time stamp that shows when the receipt was created.
If a recipient issues a receipt using a non-repudiation service, she cannot later deny having received a message. Another form of non-repudiation service is when a sender uses a non-repudiation service to obtain a receipt and a time-stamp showing when a message was created. If this receipt is attached to the message (together with a digital signature binding it to the originator), the originator cannot later deny having created the message at the time shown by the time-stamp. Applications of this can for instance be when signing contracts or writing a letter of debt.
During data transfer, confidentiality can be protected using encryption. However, when storing and managing information, encryption is often not used. Neither does encryption offer protection against all threats, for instance malicious erasure of data. Instead, sensitive information is locked away and an access control system guards who may and may not access the data. A good example of sensitive information is encryption keys used for software encryption. Another example is that it should be possible for a user to restrict the access by others to e-mail and other private material. Other concerns may be that expensive resources such as plotters and colour-printers might be misused, or that a software license limits the number of users who can use a program. Some systems store and process classified or secret information. In such systems measures must be taken to make sure only authorized users have access.
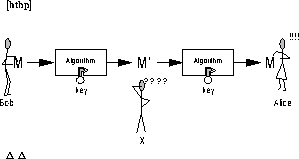
Figure 2.5: Main components in an access control system.
The generic name for a mechanism to achieve all this is access control. Figure 2.5 shows the principal components in an access control system. In standard terminology, the user or program that wants to make an access is called initiator. The program, file, or other resource that is to be accessed is called target. The access itself is called operation. To get a functioning access control system, all requests to perform operations must pass through the access control enforcer. For each request, the enforcer makes a decision to either allow or disallow the requested operation based on available access control information (ACI). Access control is described in greater detail in section 6.3.



